Phishing emails are by far one of the most dangerous threats to any Rockwall, Texas company. They are the main conduit used to infect company networks with viruses and malware, inject malicious code into a system, and steal login credentials.
Over 80% of all cyberattacks begin with a phishing email. Attackers can get right in front of an unsuspecting user without much effort at all. They can send millions of these dangerous messages in minutes, and only need a small percentage of people to take the bait for the attack to be worth the time.
While phishing may have begun two decades ago with long rambling letters from a “Prince” in a far-off land, today, it’s almost impossible to tell a phishing email from a real Amazon order notice or email from a vendor you use.
Because a majority of attacks are delivered via phishing, it’s vital to put cybersecurity safeguards in place to both detect and thwart attacks. This is also important for data privacy and GDPR compliance.
These safeguards typically fall into two categories:
- User awareness tactics
- Application-based protections
By teach your employees how to spot phishing emails AND having systems in place to help reduce the amount of phishing coming into an employee inbox, you can better protect your company from multiple types of attacks.
We’ll go through several tips below in both categories.
User Awareness Tactics
Hover Over Links Without Clicking
Phishing emails are often cleverly disguised using the logo and signature of a well-known company. If an employee receives an Amazon order email, they may immediately click the link to see what’s going on before even thinking about it.
Links to malicious phishing sites are often hid behind buttons and other images in an email. These links can take users to fake login pages (to steal their password) or sites that immediately infect their system with malware.
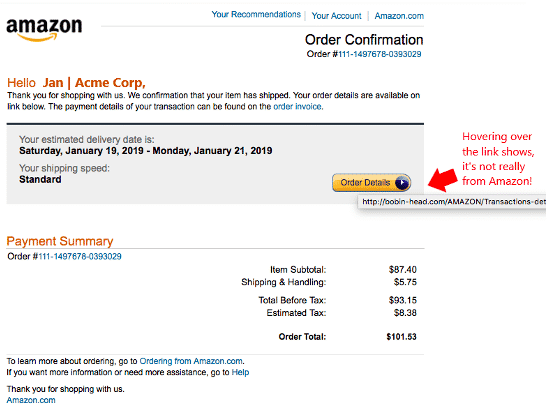
One way to identify a phishing email is to hover over links without clicking on them to reveal the true URL. This can immediately unmask a phishing scam.
Don’t Trust the Sender’s Email
Email spoofing is a tactic that is used often in phishing emails. The scammer will put a legitimate email domain in the “From” line of an email, which makes the user think it’s from a trusted company (such as their web hosting service).
This often fools people into taking whatever action is requested in the email, such as resetting a password or opening a file attachment.
Employees need to know that they can’t trust an email just because the sender’s address looks legitimate. To reveal the true sender, they should view the source code of the message in their mail application.
Suspect Anything Unexpected
People often trust emails that come in by default until they’re given a reason not to. But while some phishing does still contain grammar and spelling errors, a majority do not, making them harder to spot as fakes.
It’s important to take a stance where you are suspicious of any incoming email that is not expected and assume that it could be phishing unless proven otherwise.
It’s a good rule of thumb to double check unexpected emails, such as a holiday schedule that arrives from a vendor. A quick phone call to confirm the email is legitimate can save thousands of dollars and days of downtime from a ransomware infection.
Application-based Protections
Email Spam & Phishing Filter
You can reduce the number of phishing emails that employees have to deal with by putting an email spam and phishing filter in place on your mail server. These are designed to detect and quarantine any potential junk or phishing emails.
This both reduces the spam that employees must take time going through and the risk that an employee will accidentally click on a phishing link, because it keeps threats out of inboxes.
DNS Filter
A majority of phishing these days uses links to malicious sites instead of file attachments to get past antivirus programs. DNS filtering reduces the risk of a web-based infection by blocking malicious sites.
Even if an employee accidentally clicks on a phishing link, the DNS filter will block them from going to the site and redirect them to a warning page instead.
Monitored Antivirus/Anti-Malware
Using managed IT services with monitored antivirus/anti-malware ensures that your systems are being kept updated so they can detect the newest threats.
If an employee accidentally opens a malicious file attachment, a monitored antivirus solution can alert your IT pro of a threat right away, so it can be quarantined and removed immediately, keeping you from suffering a major breach.
Make Cybersecurity Easy With Help from Leverage IT Group
Leverage IT Group can take the burden of IT security off your shoulders by deploying multiple safeguards and keeping your network monitored at all times against threats.
Contact us today to schedule a free consultation. Call (469) 458-0559 or reach us online.

