According to Forbes, the average Windows computer has 10 weaponized vulnerabilities. A weaponized vulnerability is when a hacker realizes there is a code vulnerability in some part of an operating system and then uses that to perpetrate an attack.
Vulnerabilities are unfortunately part of life working with technology. They exist in all types of software, mobile apps, browsers, and operating systems, like Windows or macOS.
As soon as a hacker finds one of these vulnerabilities, they create what’s called an “exploit” to take advantage of the weakness in the code.
These vulnerabilities and exploits can get quite complicated, but the end result is that a user’s system can be breached if a code fix isn’t applied. These fixes usually come as soon as a hacker’s exploit is discovered and issued via an operating system (OS) or software update. This is why update management is so important to cybersecurity.
An example of an exploit that takes advantage of a Windows vulnerability is the exploit named CVE-2019-1336. This exploit takes advantage of a weakness in how the Windows Update Client handles user privileges. The exploit can take advantage of this by elevating the privilege of a user to allow a hacker to control high-level system settings.
Exploit Kits
One other term you’ll hear is “exploit kit.” An exploit kit bundles several of these exploits together into one malicious package. Then when a user inadvertently downloads malware with that exploit kit, it can see what type of system it’s on, what has and hasn’t been updated, and choose from the kit, which exploits match that particular computer’s vulnerabilities.
Microsoft has a great graphic that explains how exploit kits work:
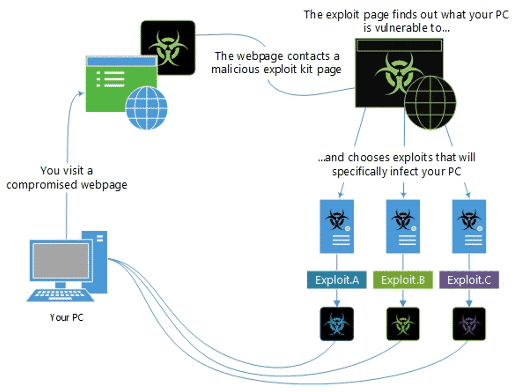 Image from Microsoft
Image from Microsoft
What Are Some of the Newest Windows Vulnerabilities?
You’ll notice that in the name of an exploited vulnerability is a year. This is an indicator of when the Windows vulnerability and exploit were first detected.
Here are some of the most recent Windows 10 vulnerabilities that can put your devices and network at risk.
CVE-2020-120: Adobe Font Manager Library Remote Code Execution Vulnerability
This vulnerability allows a hacker to take advantage of a weakness in the code for the Windows Adobe Type Manager Library. The attacker can convince a user to open a specially crafted document or install a program on their system.
CVE-2020-0965: Microsoft Windows Codecs Library Remote Code Execution Vulnerability
This vulnerability is connected to how objects are handled in memory and makes it possible for a hacker to execute arbitrary code (like ransomware or spyware) on a device.
CVE-2020-0948: Media Foundation Memory Corruption Vulnerability
This is another vulnerability that has to do with how objects are handled in memory by a Windows process. When successfully exploited, a hacker has free reign to:
- Install programs
- View, change, or delete data
- Create new user accounts with full rights
CVE-2020-0687: Microsoft Graphics Remote Code Execution Vulnerability
This code problem is related to the Window font library and how it handles embedded fonts. Exploiting this vulnerability allows a hacker to change user rights on a system, view, change and delete data, and send users to malicious websites.
CVE-2020-1135: Windows Graphics Component Elevation of Privilege Vulnerability
This vulnerability allows a hacker to run processes on a system and essentially do a full computer takeover.
What the Best Way to Fix Windows Vulnerabilities?
As soon as an exploit to a vulnerability is detected, Microsoft will put together a patch and send that out via an update.
Computer updates can contain all sorts of operating system enhancements, such as:
- Feature upgrades
- Security patches for vulnerabilities
- Bug fixes
- Compatibility upgrades
It’s vital that you keep all your devices updated as soon as these updates come out, so any newly found vulnerabilities can be patched. One of the easiest ways to do this for all your employee devices, in-office and remote, is through managed IT services.
If you leave computer updates to your employees to install, you’ll end up with many of them putting updates off because they don’t have time to do one when the update alert first pops up or because they’re afraid an update might “mess up” their system.
When you have an IT professional handling all your updates for you, each device is updated in a way that it doesn’t interrupt your productivity. Additionally, each update is confirmed to have gone through smoothly, so your users won’t suffer any problems from an update gone wrong, which can happen when they try to do them on their own.
Most importantly, you can feel a sense of relief knowing that all your devices are receiving those vital patches to seal system vulnerabilities as soon as they’re released.
Keep Your PC’s Secured Against Any System Vulnerabilities
Leverage IT Group can keep your Rockwall, TX business secure and protected against exploits and exploit kits that take advantage of Windows vulnerabilities.
Contact us today to schedule a free consultation. Call (469) 458-0559 or reach us online.

